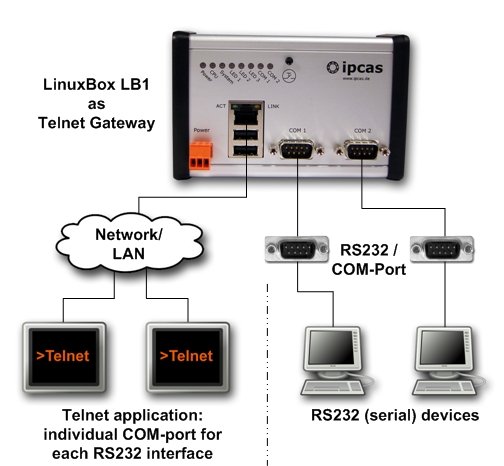
What is HTML?
HTML is a computer language devised to allow website
creation. These websites can then be viewed by anyone else connected to the
Internet. It is relatively easy to learn, with the basics being accessible to
most people in one sitting; and quite powerful in what it allows you to create.
It is constantly undergoing revision and evolution to meet the demands and
requirements of the growing Internet audience under the direction of the » W3C,
the organization charged with designing and maintaining the language. The
definition of HTML is Hyper Text Markup Language.
Hypertext is the method by which you move around on
the web — by clicking on special text called hyperlinks which bring you to the
next page. The fact that it is hyper just means it is not linear — i.e. you can
go to any place on the Internet whenever you want by clicking on links — there
is no set order to do things in. Markup is what HTML tags do to the text inside
them. They mark it as a certain type of text (italicized text, for example). HTML
is a Language, as it has code-words and syntax like any other language.
How does it work?
HTML consists of a series of short codes typed into
a text-file by the site author — these are the tags. The text is then saved as
a html file, and viewed through a browser, like Internet Explorer or Netscape
Navigator. This browser reads the file and translates the text into a visible
form, hopefully rendering the page as the author had intended. Writing your own
HTML entails using tags correctly to create your vision. You can use anything
from a rudimentary text-editor to a powerful graphical editor to create HTML
pages.
What are the tags up to?
The tags are what separate normal text from HTML
code. You might know them as the words between the <angle-brackets>. They
allow all the cool stuff like images and tables and stuff, just by telling your
browser what to render on the page. Different tags will perform different
functions. The tags themselves don’t appear when you view your page through a
browser, but their effects do. The simplest tags do nothing more than apply
formatting to some text, like this:
<b>These words will be bold</b>, and
these will not.
In the example above, the <b> tags were
wrapped around some text, and their effect will be that the contained text will
be bolded when viewed through an ordinary web browser.
If you want to see a list of a load of tags to see
what’s ahead of you, look at this tag reference. Learning the tags themselves
is dealt with in the next section of this website, My First Site.
Is there anything HTML can’t do?
Of course, but since making websites became more
popular and needs increased many other supporting languages have been created
to allow new stuff to happen, plus HTML is modified every few years to make way
for improvements. Cascading Style sheets are used to control how your pages are
presented, and make pages more accessible. Basic special effects and
interaction is provided by JavaScript, which adds a lot of power to basic HTML.
Most of this advanced stuff is for later down the road, but when using all of
these technologies together, you have a lot of power at your disposal.